One of the most useful networking tools is Nmap, which enables you to map networks, identify hosts, scan ports, identify issues with the network, find and exploit vulnerabilities, and more.
Scan Ports To Detect Services With Nmap
This tutorial’s first section describes how to find services and the software version they use by listening on open ports.
A typical Nmap scan reveals the open ports among the 1,000 most frequently used ones, as seen in the first screenshot. Nmap automatically examines the 1,000 most frequently used ports.
Protocols for relevant services are linked to ports. Nmap discovers open ports 21, 80, 443, 3306-7443 in the output shown below.
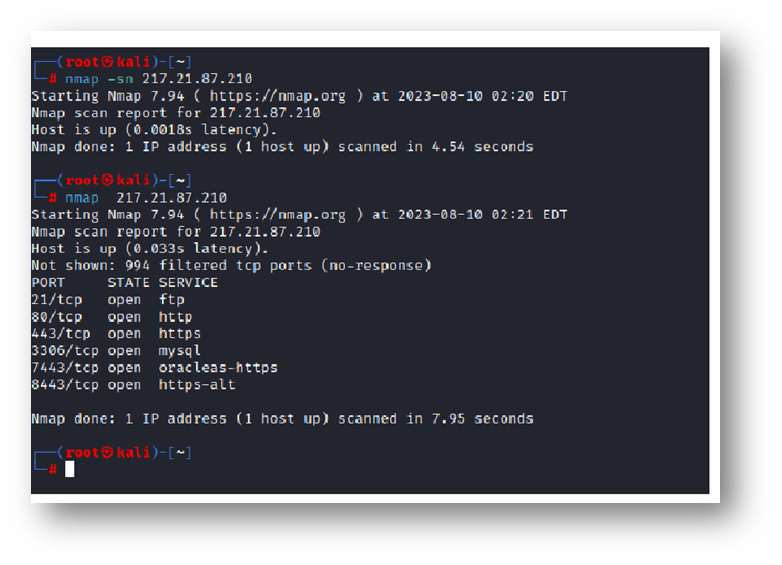
It is known to the user that ports 21, 80, 443, 3306, 7443, and 8443 are open. For instance, he is aware that port 21 is used by an FTP server. However, the customer wishes to become familiar with all other services and FTP software.
The -sV (Version) flag can be used, as displayed in the screenshot below, to identify software and versions. You can notice that ProFTPD or KnFTPD are found there.


The NSE (Nmap Scripting Engine) techniques are covered in the following section of this lesson. This real-world illustration demonstrates how to use the -script flag to include the banner grab script in the scan.
The banner grab script determines the programme version by analysing service answers.
The banner script is run in the scan that targets port 21 in the sample below, exposing the FTP server is ProFTPD.

Utilising the NSE (Nmap Scripting Engine) to find vulnerabilities
The NSE (Nmap Scripting Engine), which is covered in our NSE tutorial, is used in this section to demonstrate some methods for discovering vulnerabilities through Nmap scans.
The Nmap Scripting Engine is a collection of scripts users can add to their scans that are primarily made to find and take advantage of vulnerabilities. Users can create their own scripts to serve specific needs.
In order to ensure that Nmap is current with the most recent vulnerabilities and methodologies, the first step for the NSE scripts is to update the database.
The user can run several scripts to look for vulnerabilities after updating the database. The categories used to categorise the scripts are available at https://nmap.org/nsedoc/categories/.
In the following example, the –script flag calls the scripts from the vuln category, scanning for around 150 popular vulnerabilities.

The Nmap Scripting Engine can scan whole networks for malware-infected PCs. This is a fantastic strategy for admins to use when dealing with potential virus invasions.

Nmap is a powerful tool that can be used for both good and bad purposes. It is important to be aware of the potential risks of using nmap and to take steps to secure your systems against attack.
If You Also Want to Learn More about Ethical Hacking you can visit this

